Authenticator Plus has stated failing in recent version of Android, and appears to be no longer maintained. Specifically, the Google Backup, and the export functions no longer works. This article covers how to extract the TOTP codes from the app and import them into another app.
jonasjancarik has provided a Dockerised solution to this. The rest of the post will remain for historical purposes.`
TL;DR
-
Backup the database
-
Copy it off the phone to your computer
-
Open it with DB Browser for SQLite
-
Run the following SQL to generate the URIs
SELECT 'otpauth://totp/' || REPLACE(email, '@', '%40') || '?secret=' || secret || '&issuer=' || issuer FROM accounts; -
Generate new QR Codes to scan into your other apps
Full Details
From the technical details of Authenticator Plus we are told:
Data is stored in SQLCipher encrypted database
- SQLCipher uses 256-bit AES encryption
- Master password will be used to derive encryption key using 64000 PBKDF2 iterations(OpenSSL’s PKCS5_PBKDF2_HMAC_SHA1).
- SQLCipher uses OpenSSL libcrypto for all cryptographic functions
SQLCipher is based on SQLite, So at least we know how to decrypt the database.
Using SQLCipher from the command line was not as straight forward as I had hoped, simply because I couldn’t figure out how to communicate the cypher requirements. However, DB Browser for SQLite supports SQLCipher databases out of the box.
Getting the Database
The first step is to get the database out of Authenticator Plus. In this example I’ve just got one TOTP in my Authenticator Plus.
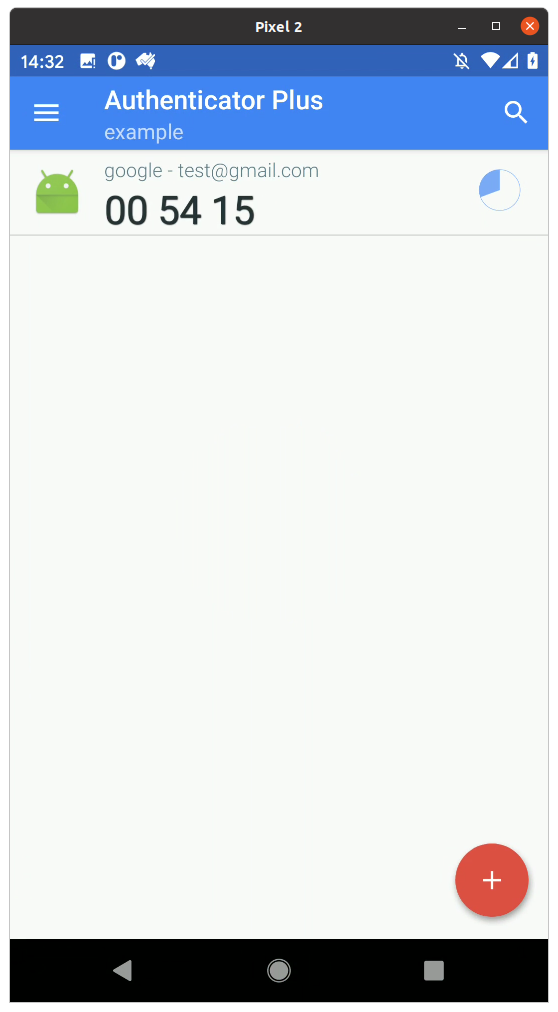
Produce a database backup by going to the Settings,
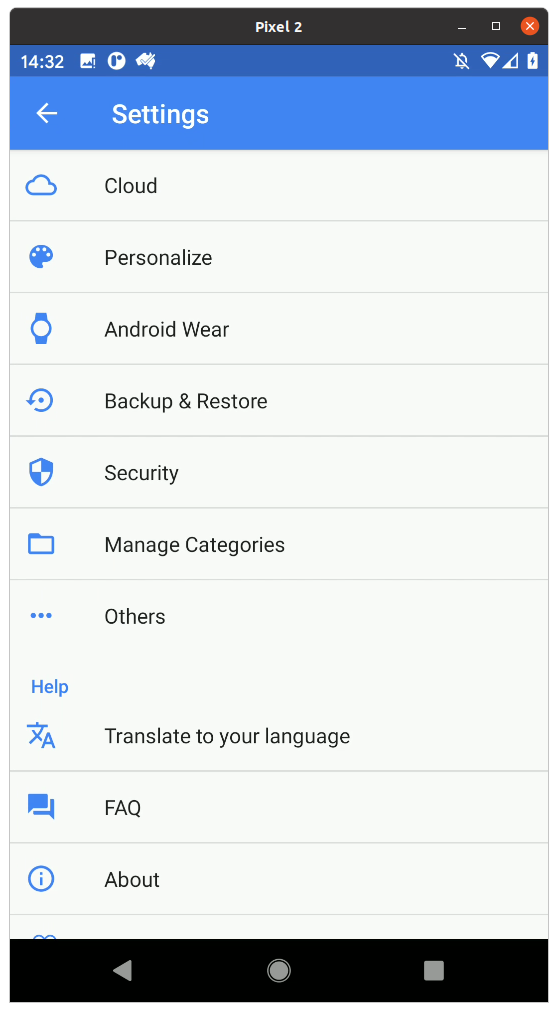
Then selecting Backup and Restore
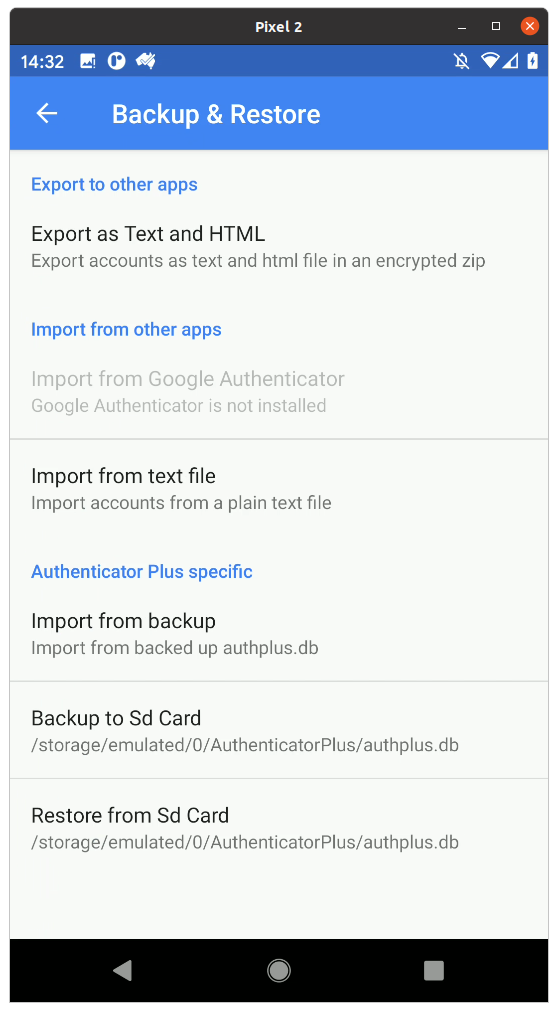
And finally selecting Backup to Sd Card.
Now, copy the authplus.db file off your phone onto your computer.
Reading the Database
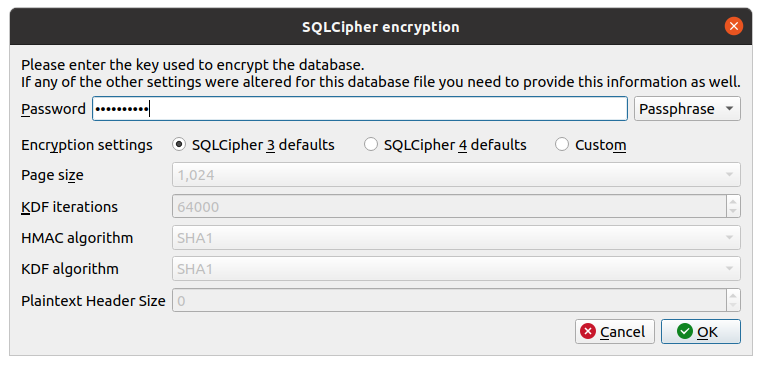
Install DB Browser for SQLite, and then open the authplus.db file. When prompted, select SQLCipher 3 Defaults, and enter your master Authenticator Plus password
Now you should have a list of tables in the database. The Accounts table is the one we want.
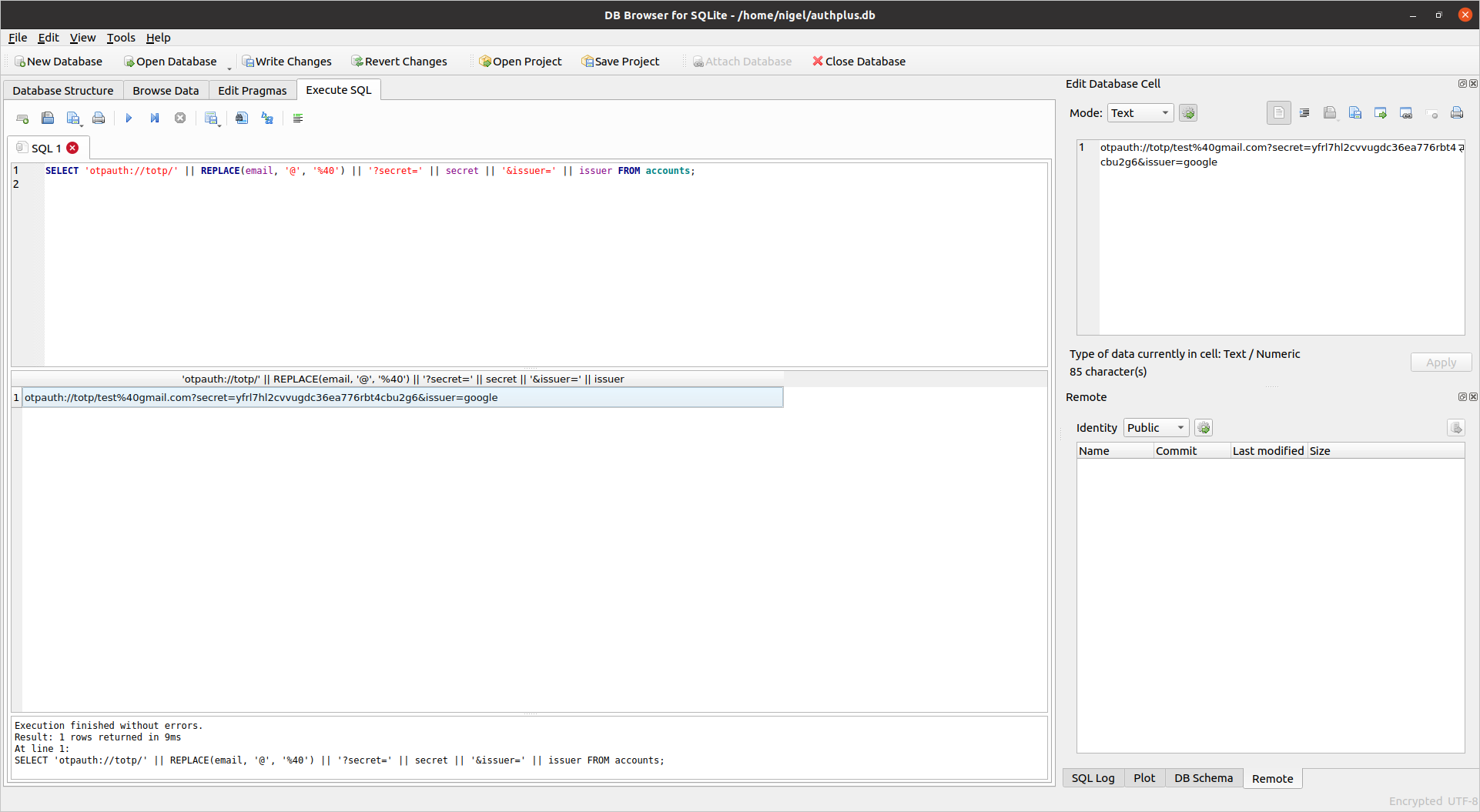
Click on the Execute SQL tab, and enter the following SQL to generate the TOTP URLs. This isn’t 100% robust as there is not a full URL escaping function available, so I’ve just converted the @ symbol. You may need to include others, or fix the URLs by hand in some situations.
SELECT 'otpauth://totp/' || REPLACE(email, '@', '%40') || '?secret=' || secret || '&issuer=' || issuer FROM accounts;
Generating QR Codes
Now, you need to convert these back into QR codes so you can scan them back into another authenticator app. One way to do this is using the following Python script. You’ll need to do this for each QR code, then display the image and scan it in.
pip install pillow qrcode
import qrcode
image = qrcode.make('otpauth://totp/test%40gmail.com?secret=yfrl7hl2cvvugdc36ea776rbt4cbu2g6&issuer=google')
image.save('totp.png')
